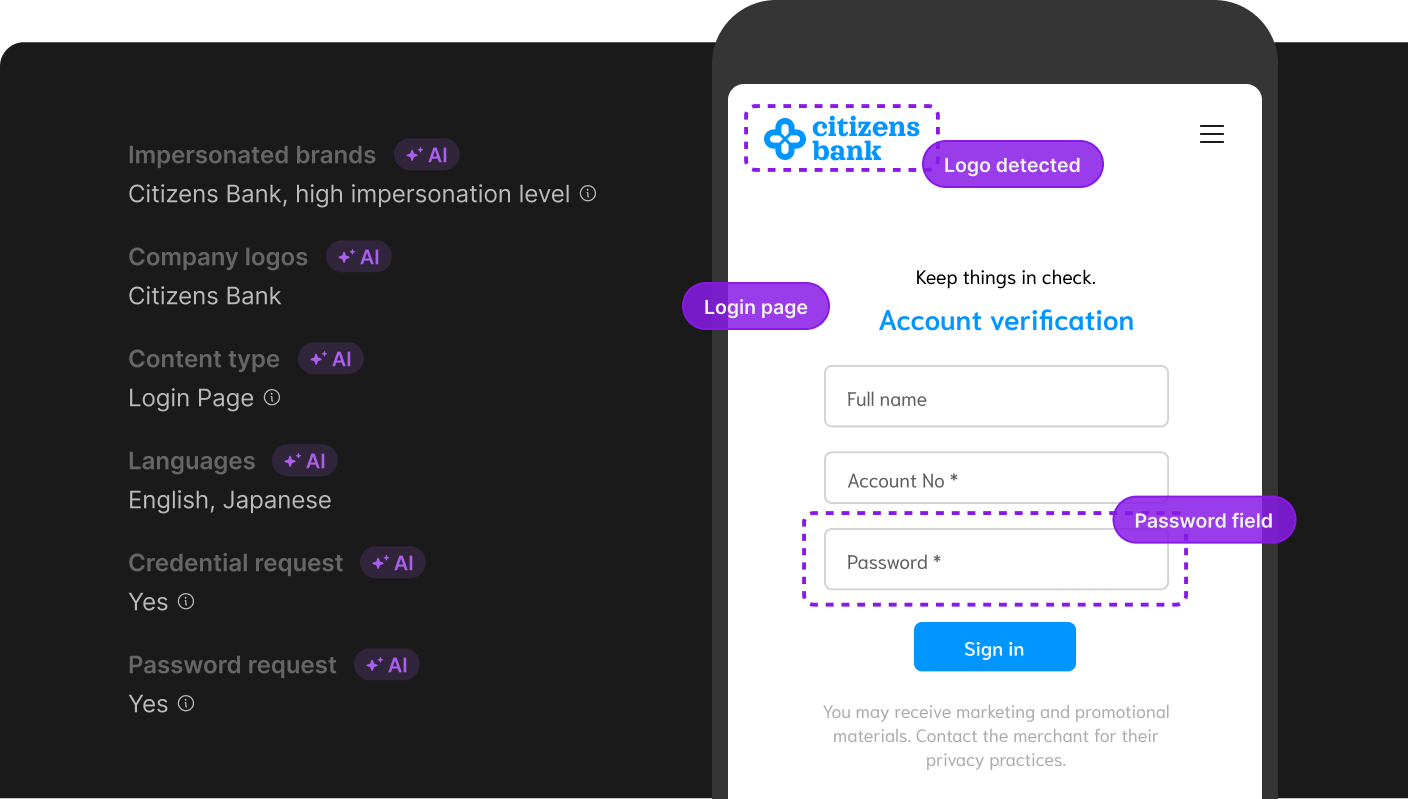
Axur monitors URLs/domains, malware, paid search/ads, social media, fake profiles, and app stores, in addition to other external sources. Our multimodal AI (vision + language) analyzes images, text, and page structure to detect fraud even without direct textual mentions of your brand. With a massive intake of 40+ million new sites per day, Axur spots fake login pages, typosquatting domains, misleading ads, fake profiles, and fraudulent apps — and prioritizes them for action.